Get to know our management systems
In Pirani we want you to manage your risks in an integral way, that's why we introduce you to our risk management systems for operational risks and information security.
What are management systems?
When creating an account you will now have the option to choose which management system you want: Operational Risk Management (ORM), Information Security (ISMS), Anti-Money Laundering (AML), Compliance.
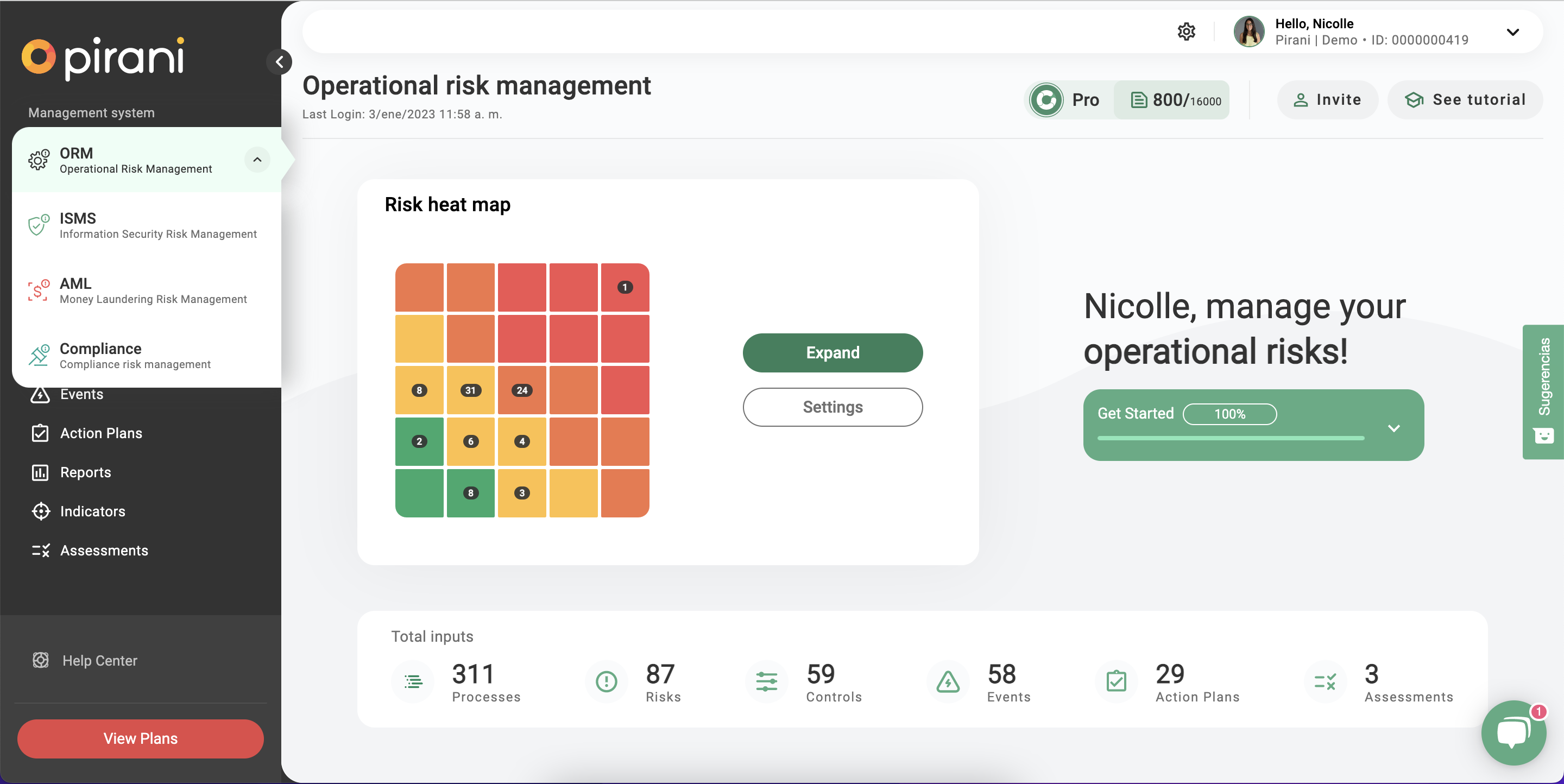
Create the new account organization
When creating an account you will now have the option to choose which management system you want: ORM (Operational Risk), Information Security (ISMS) or both.
ORM (Operational Risk Management)
These are the modules that you can find from the Operational Risk system:
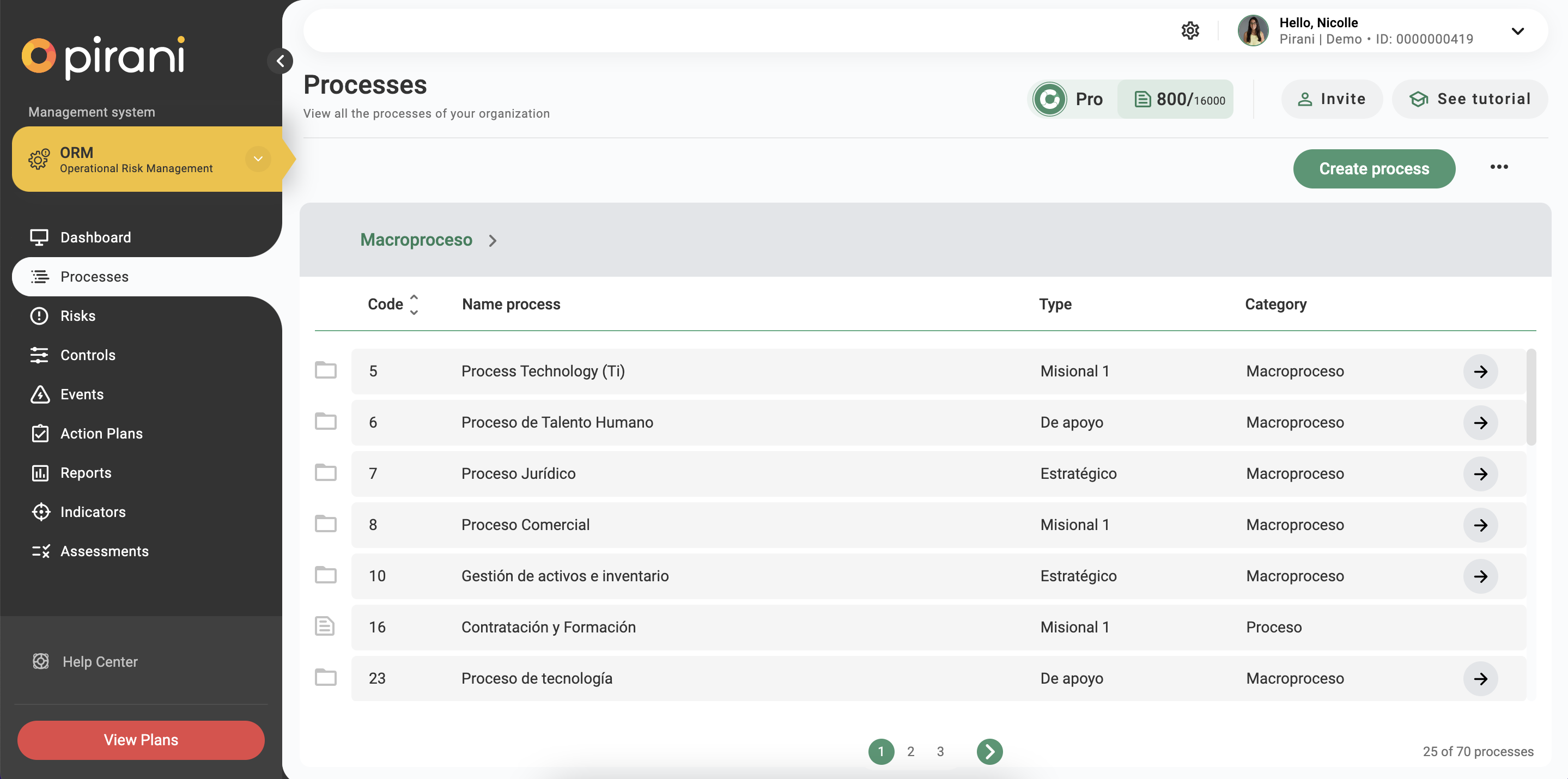
Processes: You will be able to register the process, assign the type and category it has, describe in detail what it consists of, associate it with risks and designate the person responsible for the process.
Risks: Register all the potential threats to which your company is exposed, classifying their impact and frequency, associating processes and controls and designating those responsible for the risk.
Controls: Record all the controls you consider necessary to prevent, detect or correct risks to which your company is exposed, you will also be able to qualify them through design, execution and robustness and finally, you will be able to associate risks and those responsible for supervising these controls.
Events: Register and invite members of your organization to report events and thus start promoting a risk culture.
Action plans: Create plans that have tasks assigned to specific people, a start or end date and a status that will help you understand the stage of progress.
Reports: Visualize and compare in a short time the organizational risk profile, process risk, control strength, heat map, events by criticality and event ranking (you can now also filter by management system in all your reports).
Parameterization: You will be able to parameterize the heat map and controls transversely. On the other hand, import functionalities, fields and risk rating will be done by management system.
Organization: Manage your organization's users and responsible teams in the same way for both management systems. You will be able to distinguish the authorizations you give to users through "Roles" where you can specify which module per system the person will be able to access.
ISMS (Information Security Risks)
As in the Operational Risk system, in Information Security you will find the module of processes, risks, controls, events (called incidents), action plans, reports, parameterization and organization. The variant in this system is the "Information Assets" module.
Information assets: Records any component (whether human, technological, software, etc.) that supports one or more business processes of a business unit or area.
AML (Anti-Money Laundering Risks)
Here you will also find the modules of processes, risks, controls, action plans, reports, parameterization, and organization. The variant in this system are the sections of "Associated Risks", "Risk Factors", and "Clients and Counterparties" and also does not have the events module.
Associated Risks: With this module, you will have a rating based on associated risks that you can parameterize according to your organization's methodology.
Risk Factors: Evaluate and identifies risks based on the typical risk factors your organization has.
Clients and counterparties: Identify your organization's clients and counterparties.
Compliance
In this management system you will always find the modules of processes, risks, controls, events, action plans, reports, parameterization and organization. The variant in this system is the "Standards" module.
Standards: In this module you will be able to add any type of standard both internal and external that affects the organization.